How big is the SD-WAN market, really? It depends on whom you ask:
- IDC also speculates that, based on U.S. survey data, nearly half of all enterprises will be considering a migration to SD-WAN next year, while Gartner sees only 25% of enterprises adopting it in the next two years.
Why such vastly different valuations of the same market? Perhaps because no one really agrees on how to define SD-WAN or who needs to use it.
WHAT IS SD-WAN?
In theory, SD-WAN is what its name suggests: a way of software-defining the enterprise WAN, as opposed to the traditional hardware-centric model.
SD-WAN is a response to the shift in business application architecture from the data center to the cloud, allowing enterprises to connect their end-users in a safe and reliable way to their third-party cloud platforms and SaaS applications.
However, SD-WAN isn’t, in most cases, as simple as just a software-defined on-ramp to a private network – it comprises both hardware and software, and the methods in which it is delivered and by which it performs differ from company to company.
The large number estimated by Research and Markets included:
“SD-WAN hardware that includes appliances and routers, SD-WAN software that includes orchestrators, gateways, cloud routers and firewalls, dashboards, management systems among others, and SD-WAN services that includes Service Provider Managed SD-WAN services and Cloud Managed SD-WAN services.”
The Gartner report details sixteen different vendors, and no two are exactly alike. Some offer overlay and others in-net, there are both regional and global SD-WAN, and you can pay for a managed service or provision the extra resources to do it yourself. So how are you to make heads or tails of which solution is right for you?
OVERLAY OR IN-NET?
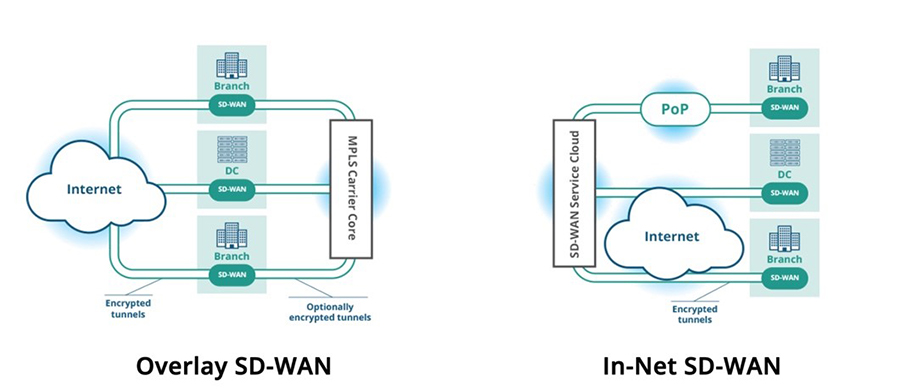
One of the reasons why P&S Market Research, Research and Markets, and IDC may see such a high market valuation for SD-WAN is the amount of hardware you might need to purchase to manage your service. Most SD-WAN sit at the edge and require some hardware for deployment.
As Gartner writes:
“Many SD-WAN deployments today haven’t actually replaced traditional routers; they’ve supplemented them for a variety of reasons, including risk aversion and lack of support for legacy T1/E1 interfaces.”
These edge-based SD-WAN are considered “overlay” SD-WAN, where they function as a routing devices between your MPLS and the public Internet. Overlay SD-WAN is location-independent and makes connectivity more interchangeable, while optimizing the last mile.
However, because some SD-WAN following this model do not replace the router but add a box, your budget may need to expand to accommodate the hardware and its maintenance and monitoring. The same applies if Ethernet is not available.
An OpEx model may not be an option, and the system must be managed by the IT team.
In-net SD-WAN, on the other hand, while less common, can offer more flexibility. In-net SD-WAN covers the middle mile, and it can be delivered through what Gartner calls a “cloud-based OTT” model or provide appliances for additional functionality at the edge.
The in-net model, because it provides its own WAN and allows organizations to subscribe to use the WAN as-a-service, can optimize the middle mile for Internet connected sites globally, and new functionalities can be delivered via cloud, without asking users to upgrade hardware.
The only drawbacks for this model appear if the IT team prefers a DIY “construct” model for their WAN, as opposed to a “consume” model, where the network is delivered as-a-service.
REGIONAL OR GLOBAL?
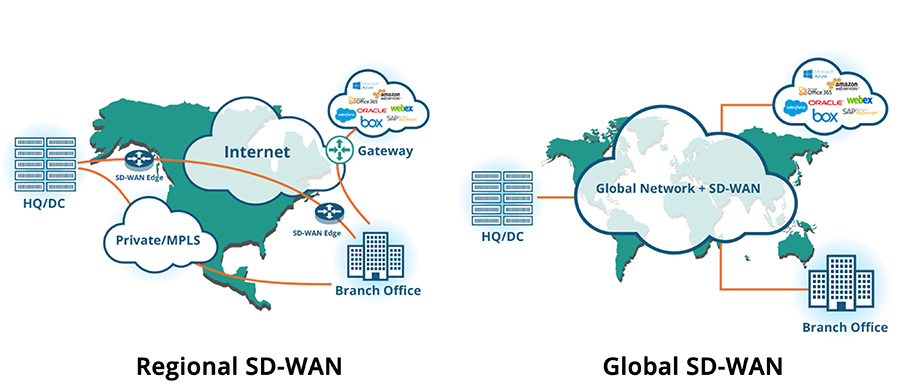
Most SD-WAN can still only support regional deployments because they rely only on the Internet and don’t include custom-built private networks for fast cloud and SaaS connectivity. Although it can reduce network complexity and lower network costs at a branch office by replacing regional MPLS through aggregate Internet links, SD-WAN at the edge does not optimize traffic over the middle mile.
And when offices are collaborating and communicating in real-time, or attempting to connect to applications housed in other geographies, regional SD-WAN presents a real latency challenge.
For an SD-WAN to fully tackle those challenges on a global scale, it must leverage a private network that is layered over the Internet to accelerate data and application performance. In that way, the SD-WAN can replace MPLS by combining a private network in the middle mile and Internet at the edge, while still providing MPLS-grade connectivity in all geographies where business is conducted, delivered via privately owned and maintained points of presence (POPs).
Regional SD-WAN can serve the needs of businesses with branch offices that don’t cross oceans or users that work from remote geographies; however, global enterprises or enterprises that have the potential to scale should consider a global SD-WAN solution to maximize application performance and data transfer anywhere in the world.
DIY OR AS-A-SERVICE?
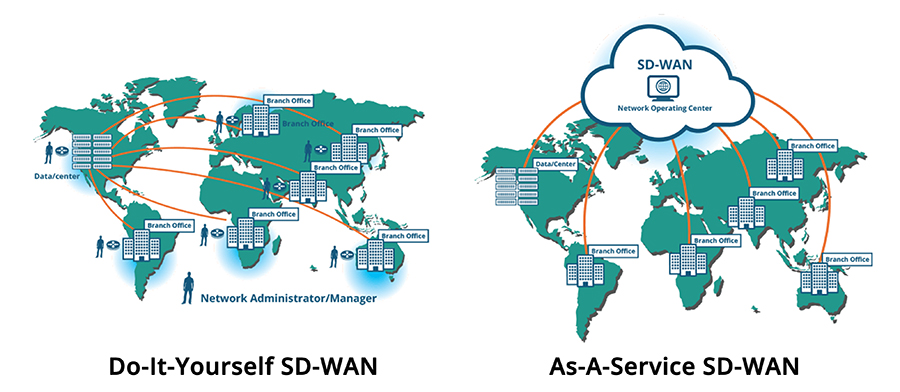
As I mentioned earlier, some IT departments prefer to construct their own network, as opposed to consume a ready-made model.
Even in a DIY situation, WAN management software from DIY SD-WAN vendors can make the orchestration of network services easier at the branch; however, the IT department then must deal with multiple vendors and contracts. In this case, the management of these networks becomes resource-intensive, and integration of new branch offices or links can become a hassle, especially when dealing with large global network scenarios.
In the as-a-service or cloud-based OTT model, the solution is fully integrated. WAN management is taken care of by the as-a-Service SD-WAN provider, freeing up IT resources and budget for other projects.
While the consume model is not for every enterprise, some SD-WAN providers make it possible to customize the services delivered to meet the needs of the purchasing organization in order to best meet their needs with a complete solution.
SO, HOW BIG IS THE SD-WAN MARKET, REALLY?
In the end, it doesn’t matter if the solutions available don’t fit your needs.
As a global enterprise looking to maximize your investment, free up IT resources, and improve application performance throughout the whole network and not just at the edge, the best bet is to work with a global SD-WAN provider with a private WAN.
ARYAKA GLOBAL SD-WAN
Aryaka’s global SD-WAN delivers the application performance requirements for today’s cloud and SaaS environments to enterprises with a worldwide presence. Our MPLS-grade global private network was built with full-mesh connectivity on 28 points of presence (PoPs) on all six habitable continents and layered with WAN Optimization, creating an MPLS-grade global private network that accelerates application performance and practically eliminates congestion and packet loss.
Aryaka’s global SD-WAN is also delivered as a service, so you don’t have to buy, configure, deploy, or maintain expensive WAN Optimization boxes in every single location. This approach delivers cloud and SaaS applications to global end-users as if those applications were living in the local corporate data center and can be deployed in a matter of hours, instead of months or years.




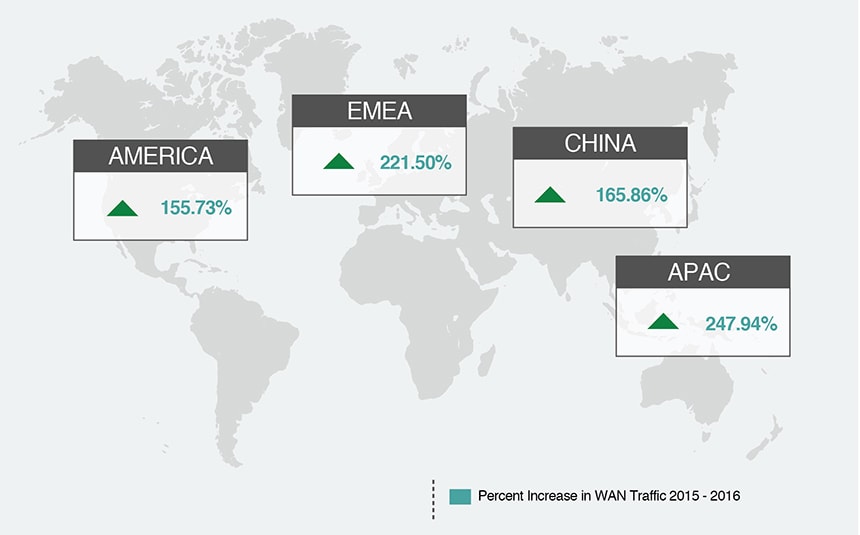 According to the 2017 State of the WAN Report, enterprise WAN traffic grew by an average 200% worldwide.
According to the 2017 State of the WAN Report, enterprise WAN traffic grew by an average 200% worldwide.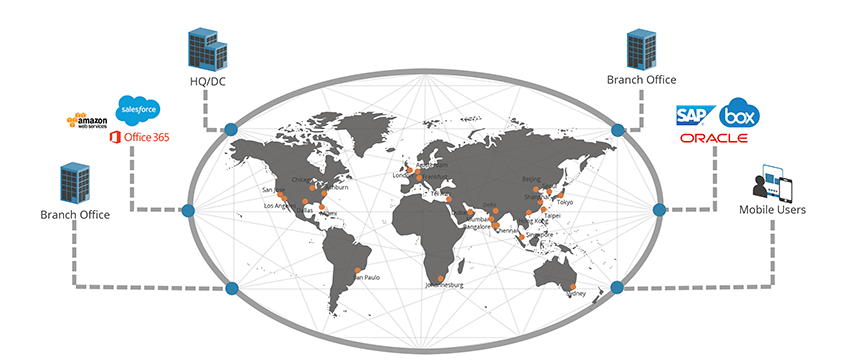 Aryaka Global SD-WAN
Aryaka Global SD-WAN