Cloud Web Security
SECURITY STACK AS A SERVICE
WHAT ARE YOU PROTECTING?
Traditional network security made sense when all corporate applications were hosted in the data center and users were all on the network. But with apps moving to the cloud, and users increasingly mobile, reality has changed. Architectures back-hauling traffic to a centralized location, just for security, are costly and complex, just like spreading security stacks in every location for a Hub and Spoke architecture, all are increasingly ineffective, costly and irrelevant. These models force all traffic through centralized data center stacks for security and access controls—a complex configuration that results in a terrible user experience.
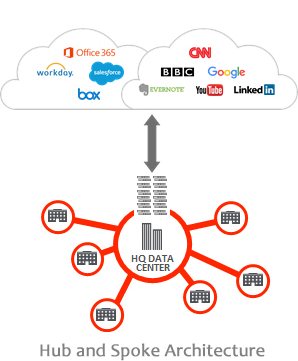
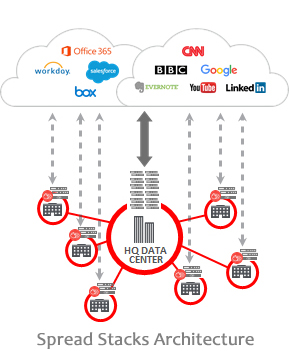
As applications move more and more to the cloud, the center of gravity moved with it. User traffic often goes straight to the cloud, bypassing the security perimeter and creating a great challenge for IT managers and CSOs. Security is required around users, not networks.
WHAT ARE YOU PROTECTING FROM?
Today’s complex threats, malwares and infected websites, all triggered an explosion of new security appliances, all finding their way into your overworked gateway. Administrators are in a constant battle to keep up with required security updates for their appliances. The complexity of deploying and managing all these appliances — and their associated costs — are out of control. Furthermore, it is all associated with what is now an outdated architecture.
IMPROVE PERFORMANCE, REDUCE COST AND COMPLEXITY
Security stack as a service eliminates the cost and complexity of traditional secure web gateway approaches. By moving security to a globally distributed cloud, it brings the Internet gateway closer to the user for a faster experience. Organizations can easily scale protection to all offices or users, regardless of location, and minimize network and appliance infrastructure.
FIT YOU ECOSYSTEM
With multiple systems spread around organization, it is crucial to integrate systems for ease of management as well as for completing business ecosystem to maximize benefit from each system. This refers to Identify Providers, Mobile Device Management systems, SIEM servers etc.
PROVIDE UP-TO-DATE SECURITY
With the security stack threat intelligence being in the cloud, it benefits from millions of users working for you. Updates can go over 100K updates a day, so that any threat detected anywhere in the cloud is immediately blocked for all nodes.
OUR SOLUTION
We provide organizations with a Secure Internet Service – Zscaler Internet Access. All you do is make us your next hop to the Internet. No matter where users connect — a coffee shop in Milan, a hotel in Hong Kong, or the office — they get identical protection.
The service sits between your users and the Internet, inspecting every byte of traffic inline across multiple security techniques, even within encrypted, SSL/HTTPS traffic. You get full protection from web and Internet threats. And with a cloud platform that supports Cloud Sandboxing, Next-Generation Firewall, Data Loss Prevention (DLP), and Cloud Application Visibility and Control, you can start with the services you need today and activate others as your needs grow.
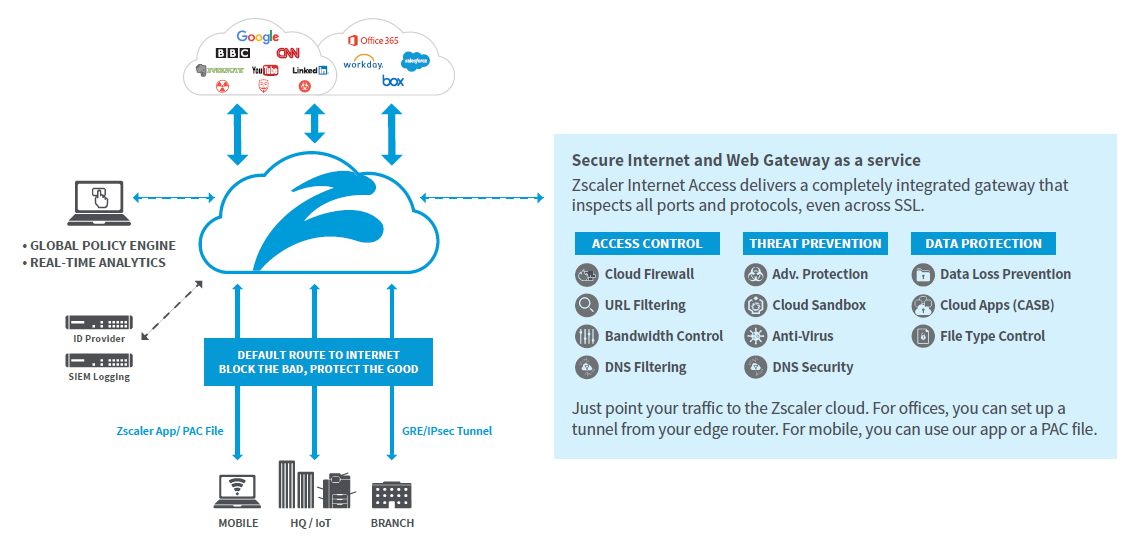
WHY CLOUD PROTECTS BETTER THAN APPLIANCES?
We deliver the DMZ as a service, with AV inspection, next-gen firewall, sandbox, advanced threat protection, URL filters, SSL inspection, and more —all in a unified platform service. It’s airtight security without the cost and complexity of stacks of appliances, and it delivers a fast, secure user experience, whether users connect from an office, coffee shop, or airport, at home or abroad.
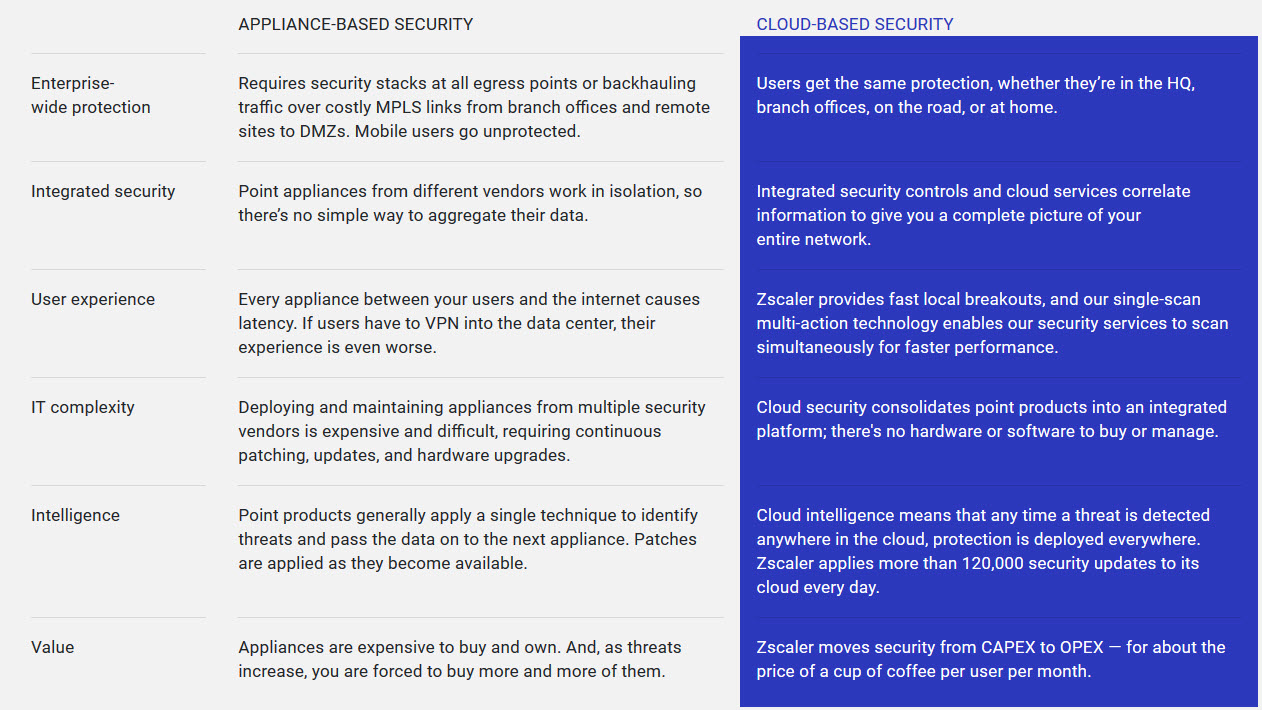
Protecting users with consistent and enforceable policies requires much more than simple URL or web filtering. That’s why thousands of organizations have already moved their IT security from appliances to security controls in the cloud. Here are some of the differences between appliance-based security and a cloud-delivered approach.
DELIVERED FROM THE WORLD’S LARGEST SECURITY CLOUD
Our cloud is deployed in 100 data centers across 5 continents. So for instance, your employees sitting in Brazil go through the Brazil data center and employees sitting in India who go to Mumbai connect to the local data
center. The number of threats and level of innovation and sophistication is increasing rapidly, so you must be able to evolve your cloud to handle more frequent updates. Appliances were never designed for this frequency of updates. We do about a120,000 unique security updates every day. Imagine trying to update an appliance 120,000 times day.
We also peer with all leading Internet exchanges and leading apps, ranging from Office 365, to Azure, AWS, Box and Salesforce. This helps you get the fastest performance because our data center sitting in Chicago and New York are peered with the content, giving you fastest connection from our cloud.
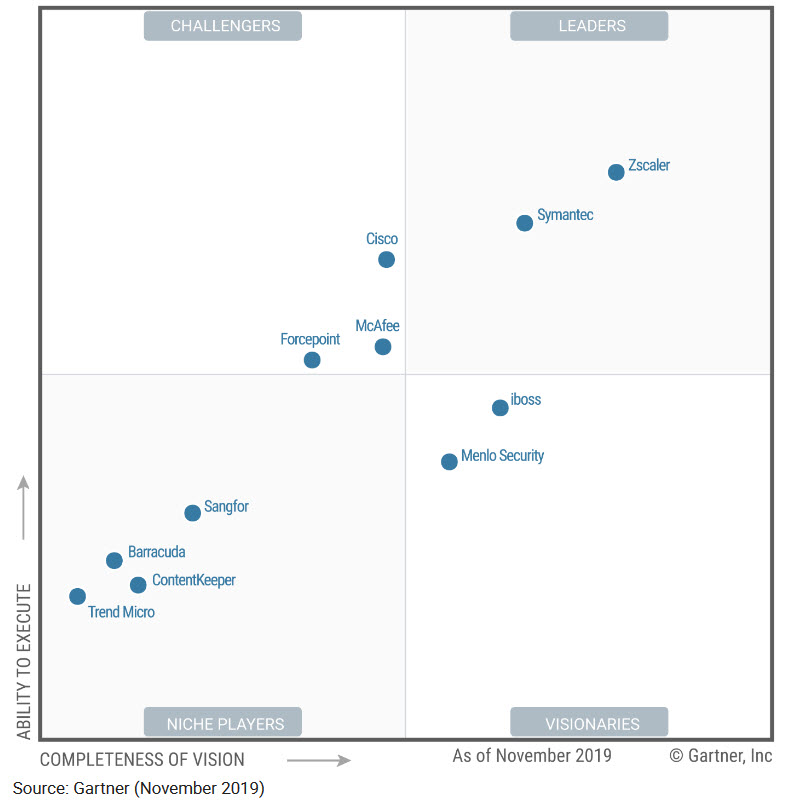
ZSCALER – NAMED LEADER FOR THE 9TH YEAR IN A RAW
For now 9 years in a raw, Gartner named Zscaler as a world leader in the Magic Quadrant for Secure Web Gateways.
Download the 2019 Gartner Magic Quadrant for Secure Web Gateways here.
How good is YOUR Internet Security?
Get a quick assessment of the strength of your Internet security. You will see how well your security infrastructure can stop threats, protect your users, and safeguard your company data. It will also provide recommendations on how to close any gaps that are found.
Despite costly on-premises security appliances (such as Cisco, Symantec/Blue Coat, Websense/Forecepoint, McAfee, Check Point, FireEye, Fortinet, Palo Alto Networks) many enterprise networks still remain vulnerable due to functionality, performance, or misconfiguration issues. With a global security cloud that processes billions of security requests every day, Zscaler instantly scans and pinpoints security gaps other security solutions often miss and can help you take corrective action today.
Want to hear more about our security solutions? Use the contact form, and we will contact you soon.



 New Gartner report on Secure Web Gateway
New Gartner report on Secure Web Gateway